k8s RBAC之基于用户组授权案例
1.RBAC基于组的方式认证
-
对用户组授权访问案例(Group)
用户组的好处是无需单独为某个用户创建权限,统一为这个组名进行授权,所有的用户都以组的身份访问资源。
需求说明: 为baimei用户组统一授权:
- 将certs.sh文件中的"baimeidashu-crs.json"下的O字段改成dev,并重新生成证书和kubeconfig文件;
- 将dev用户组绑定Role(pod-reader);
- 测试,只要O字段都是dev,对于'CN'字段可以是任意用户哟,这些用户持有的kubeconfig文件都拥有相同的权限;
举个例子:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: read-pods
namespace: default
subjects:
- kind: Group
name: baimei
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: pod-reader
apiGroup: rbac.authorization.k8s.io
(1)APIserver会优先校验用户名(CN字段),若用户名没有对应的权限,则再去校验用户组(O)的权限。
CN:
CN标识的是用户名称,比如"baimeidashu"。。
O:
O标识的是用户组,比如"dev"组。
(2)用户,用户组都是提取证书中的一个字段,不是在集群中创建的。
RBAC基于组的方式认证:
CN: 代表用户,
O: 组。
1.使用k8s ca签发客户端证书
1.1 编写证书请求
cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "87600h"
}
}
}
}
EOF
cat > baimei-csr.json <<EOF
{
"CN": "linux86",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "baimei",
"OU": "System"
}
]
}
EOF
1.2 生成证书
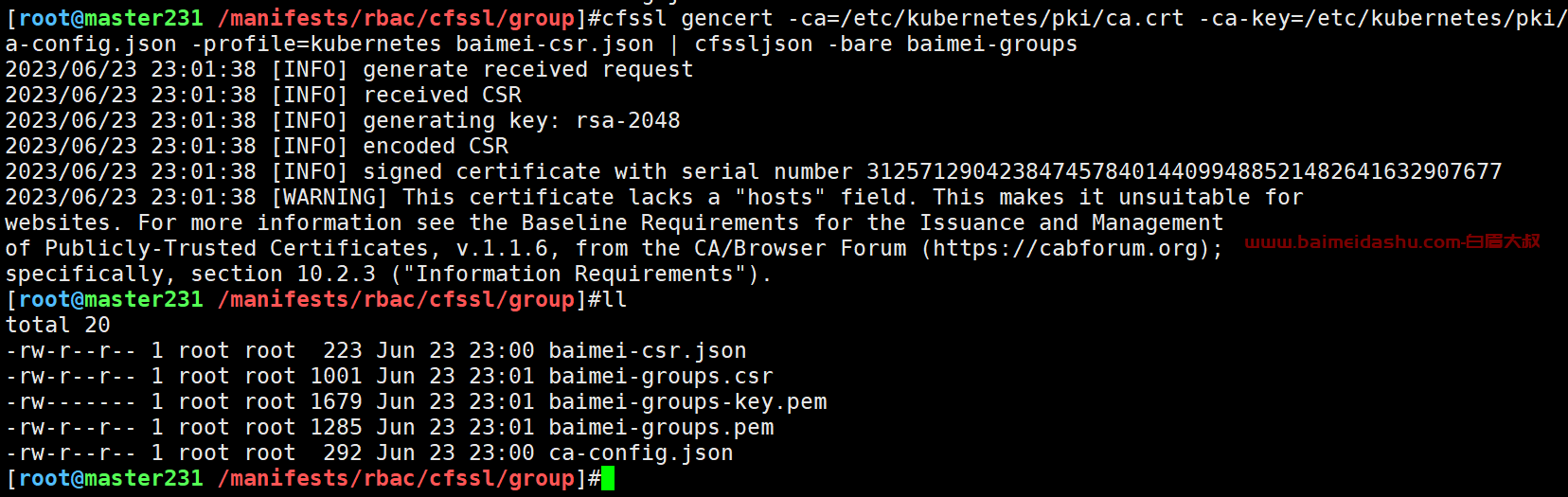
cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key -config=ca-config.json -profile=kubernetes baimei-csr.json | cfssljson -bare baimei-groups
2.生成kubeconfig授权文件
2.1 编写生成kubeconfig文件的脚本
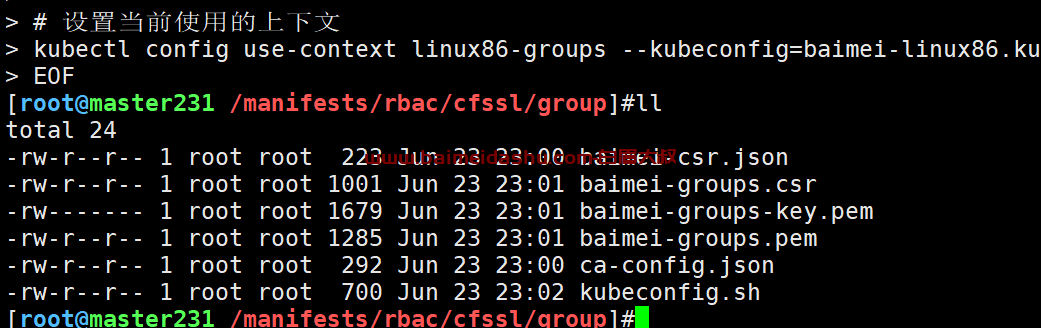
cat > kubeconfig.sh <<'EOF'
kubectl config set-cluster baimei-linux86-groups \
--certificate-authority=/etc/kubernetes/pki/ca.crt \
--embed-certs=false \
--server=https://10.0.0.231:6443 \
--kubeconfig=baimei-linux86.kubeconfig
设置客户端认证
kubectl config set-credentials baimei
--client-key=baimei-groups-key.pem
--client-certificate=baimei-groups.pem
--embed-certs=false
--kubeconfig=baimei-linux86.kubeconfig
设置默认上下文
kubectl config set-context linux86-groups
--cluster=baimei-linux86-groups
--user=baimei
--kubeconfig=baimei-linux86.kubeconfig
设置当前使用的上下文
kubectl config use-context linux86-groups --kubeconfig=baimei-linux86.kubeconfig
EOF
2.2 生成kubeconfig文件
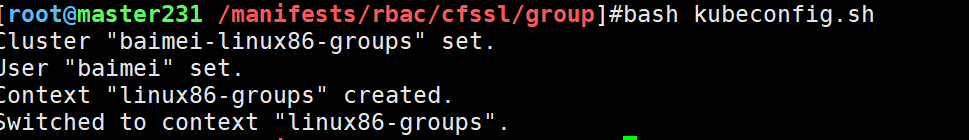
bash kubeconfig.sh
3. 创建RBAC授权策略
cat rbac.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: linux86-role-reader
rules:
# API组,""表示核心组,该组包括但不限于"configmaps","nodes","pods","services"等资源.
# 想要知道哪个资源使用在哪个组,我们只需要根据"kubectl api-resources"命令等输出结果就可以轻松判断哟~
# API组,""表示核心组。
- apiGroups: ["","apps"]
# 资源类型,不支持写简称,必须写全称哟!!
resources: ["pods","nodes","services","deployments"]
# 对资源的操作方法.
verbs: ["get", "watch", "list"]
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: baimei-to-linux84-role-reader
namespace: default
subjects:
主体类型
- kind: Group
用户名
name: baimei
apiGroup: rbac.authorization.k8s.io
roleRef:
角色类型
kind: Role
绑定角色名称
name: linux86-role-reader
apiGroup: rbac.authorization.k8s.io
kubectl apply -f rbac.yaml
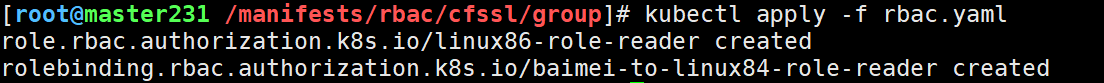
4.验证权限
kubectl get pods --kubeconfig=baimei-linux86.kubeconfig
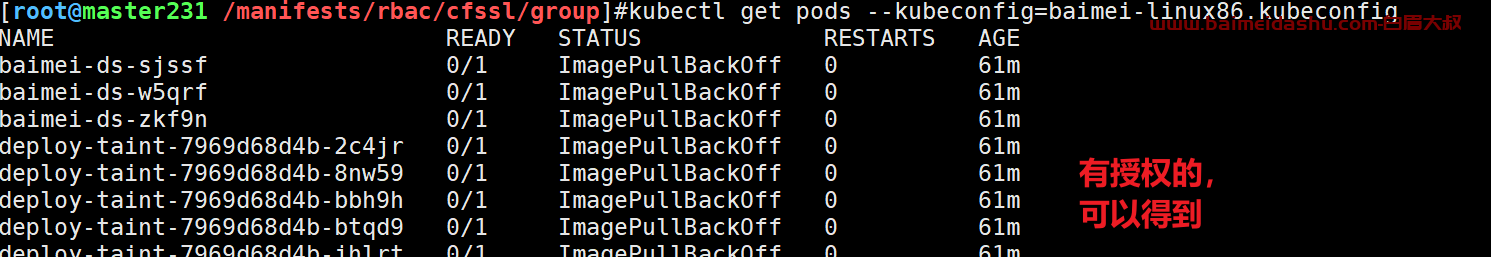
无授权操作:
kubectl delete pods --all --kubeconfig=baimei-linux86.kubeconfig
创建一个zhaozhiyong用户,其加入baimei组,并验证权限
目的:无需给zhaozhiyong授权,因为其加入了baimei组。该组是有权限
新建一个 gourp2的文件夹
1.使用k8s ca签发客户端证书
1.1 编写证书请求
cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "87600h"
}
}
}
}
EOF
cat > baimei-csr.json <<EOF
{
"CN": "linux86",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "baimei",
"OU": "System"
}
]
}
EOF
1.2 生成证书
cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key -config=ca-config.json -profile=kubernetes baimei-csr.json | cfssljson -bare baimei-groups
2.生成kubeconfig授权文件
2.1 编写生成kubeconfig文件的脚本
cat > kubeconfig.sh <<'EOF'
kubectl config set-cluster baimei-linux86-groups \
--certificate-authority=/etc/kubernetes/pki/ca.crt \
--embed-certs=true \
--server=https://10.0.0.231:6443 \
--kubeconfig=baimei-linux86.kubeconfig
设置客户端认证
kubectl config set-credentials baimei
--client-key=baimei-groups-key.pem
--client-certificate=baimei-groups.pem
--embed-certs=true
--kubeconfig=baimei-linux86.kubeconfig
设置默认上下文
kubectl config set-context linux86-groups
--cluster=baimei-linux86-groups
--user=baimei
--kubeconfig=baimei-linux86.kubeconfig
设置当前使用的上下文
kubectl config use-context linux86-groups --kubeconfig=baimei-linux86.kubeconfig
EOF
2.2 生成kubeconfig文件
bash kubeconfig.sh
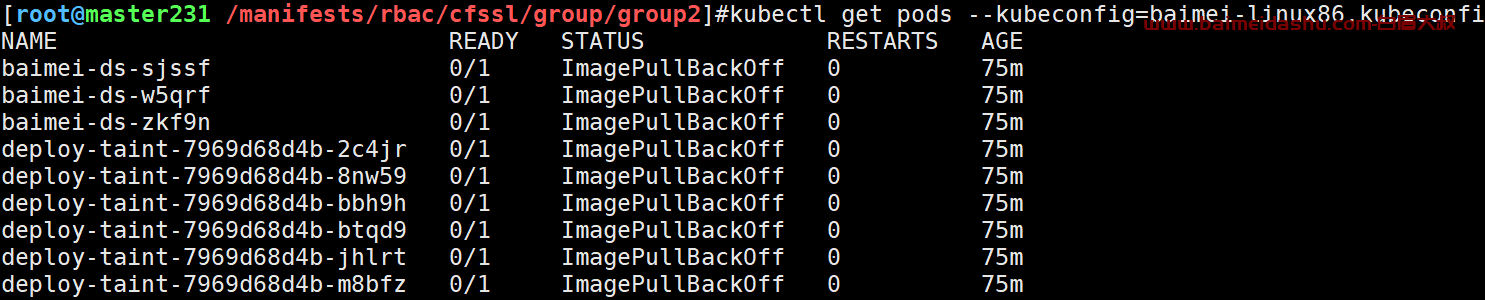
3.直接验证,无需给zhaozhiyong授权,因为其加入了baimei组。该组是有权限的!
这里并没有 设置yaml 文件哦
kubectl get pods --kubeconfig=baimei-linux86.kubeconfig
 51工具盒子
51工具盒子