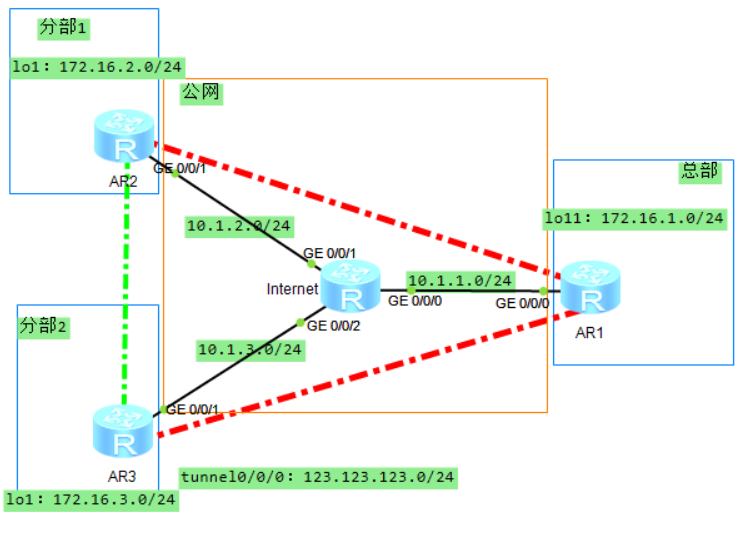
组网需求 {#组网需求}
某大型企业有总部(Hub)和多个分支(Spoke1、Spoke2......,举例中仅使用两个分支),分布在不同地域,总部和分支的子网环境会经常出现变动。分支采用动态地址接入公网。企业现网网络规划使用OSPF路由协议。
现在用户希望能够实现分支之间的VPN互联,同时对总部和分支机构以及分支机构间传输的数据进行加密保护。
配置思路 {#配置思路}
企业网络管理员可以采用如下思路进行分析:
- 由于分支是采用动态地址接入公网的,分支之间互相不知道对方的公网地址,因此必须采用DSVPN来实现分支之间的VPN互联。
- 由于分支数量较多,因此采用shortcut场景的DSVPN。
- 由于分支和总部的子网环境经常出现变动,为简化维护并根据企业网络规划,选择部署OSPF路由协议来实现分支/总部间的通信。
- 由于需要对机构之间的传输数据进行加密保护,因此采用配置IPSec保护的DSVPN来实现该功能。
注意:在DSVPN中部署IPSec时,如果两个分支位于不同NAT设备之后或者总部位于NAT设备之后,则IPSec封装模式仅支持为传输模式。
操作步骤 {#操作步骤}
配置IP地址 {#配置ip地址}
AR1 {#ar1}
<Huawei>sys
[Huawei]sys AR1
[AR1]int g0/0/0
[AR1-GigabitEthernet0/0/0]ip add 10.1.1.1 24
[AR1-GigabitEthernet0/0/0]q
[AR1]int lo1
[AR1-LoopBack1]ip add 172.16.1.1 24
[AR1-LoopBack1]q
[AR1]int t0/0/0 [AR1-Tunnel0/0/0]ip add 123.123.123.1 24 [AR1-Tunnel0/0/0]q
AR2 {#ar2}
<Huawei>sys
[Huawei]sys AR2
[AR2]int g0/0/1
[AR2-LoopBack1]ip add 10.1.2.2 24
[AR2-LoopBack1]q
[AR2]int lo1
[AR2-GigabitEthernet0/0/0]ip add 172.16.2.2 24
[AR2-GigabitEthernet0/0/0]q
[AR2]int t0/0/0 [AR2-Tunnel0/0/0]ip add 123.123.123.2 24 [AR2-Tunnel0/0/0]q
AR3 {#ar3}
<Huawei>sys
[Huawei]sys AR3
[AR3]int g0/0/1
[AR3-LoopBack1]ip add 10.1.3.3 24
[AR3-LoopBack1]q
[AR3]int lo1
[AR3-GigabitEthernet0/0/0]ip add 172.16.3.3 24
[AR3-GigabitEthernet0/0/0]q
[AR3]int t0/0/0 [AR3-Tunnel0/0/0]ip add 123.123.123.3 24 [AR3-Tunnel0/0/0]q
Internet {#internet}
<Huawei>sys
[Huawei]sys Inernet
[Inernet]int g0/0/0
[Inernet-GigabitEthernet0/0/0]ip add 10.1.1.10 24
[Inernet-GigabitEthernet0/0/0]q
[Inernet]int g0/0/1
[Inernet-GigabitEthernet0/0/1]ip add 10.1.2.10 24
[Inernet-GigabitEthernet0/0/1]q
[Inernet]int g0/0/2 [Inernet-GigabitEthernet0/0/2]ip add 10.1.3.10 24 [Inernet-GigabitEthernet0/0/2]q
配置公网路由可达 {#配置公网路由可达}
AR1 {#ar1-1}
[AR1]ospf 2 router-id 10.1.1.1
[AR1-ospf-2]area 1
[AR1-ospf-2-area-0.0.0.1]net 10.1.1.0 0.0.0.255
[AR1-ospf-2-area-0.0.0.1]q
[AR1-ospf-2]q
AR2 {#ar2-1}
[AR2]ospf 2 router-id 10.1.2.2
[AR2-ospf-2]area 1
[AR2-ospf-2-area-0.0.0.1]net 10.1.2.0 0.0.0.255
[AR2-ospf-2-area-0.0.0.1]q
[AR2-ospf-2]q
AR3 {#ar3-1}
[AR3]ospf 2 router-id 10.1.3.3
[AR3-ospf-2]area 1
[AR3-ospf-2-area-0.0.0.1]net 10.1.3.0 0.0.0.255
[AR3-ospf-2-area-0.0.0.1]q
[AR3-ospf-2]q
Internet {#internet-1}
[Inernet]ospf 2 router-id 10.1.123.10
[Inernet-ospf-2]area 1
[Inernet-ospf-2-area-0.0.0.1]ne
[Inernet-ospf-2-area-0.0.0.1]net 10.1.1.0 0.0.0.255
[Inernet-ospf-2-area-0.0.0.1]net 10.1.2.0 0.0.0.255
[Inernet-ospf-2-area-0.0.0.1]net 10.1.3.0 0.0.0.255
[Inernet-ospf-2-area-0.0.0.1]q
[Inernet-ospf-2]q
验证配置 {#验证配置}
#查看路由表
[AR1]display ospf 2 routing
OSPF Process 2 with Router ID 10.1.1.1
Routing Tables
Routing for Network
Destination Cost Type NextHop AdvRouter Area
10.1.1.0/24 1 Transit 10.1.1.1 10.1.1.1 0.0.0.1
10.1.2.0/24 2 Transit 10.1.1.10 10.1.2.2 0.0.0.1
10.1.3.0/24 2 Transit 10.1.1.10 10.1.3.3 0.0.0.1
Total Nets: 3
Intra Area: 3 Inter Area: 0 ASE: 0 NSSA: 0
#ping验证
[AR1]ping 10.1.3.3
PING 10.1.3.3: 56 data bytes, press CTRL_C to break
Reply from 10.1.3.3: bytes=56 Sequence=1 ttl=254 time=30 ms
Reply from 10.1.3.3: bytes=56 Sequence=2 ttl=254 time=30 ms
Reply from 10.1.3.3: bytes=56 Sequence=3 ttl=254 time=30 ms
Reply from 10.1.3.3: bytes=56 Sequence=4 ttl=254 time=30 ms
Reply from 10.1.3.3: bytes=56 Sequence=5 ttl=254 time=20 ms
--- 10.1.3.3 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 20/28/30 ms
配置内网路由可达 {#配置内网路由可达}
AR1 {#ar1-2}
[AR1]ospf 1 router-id 172.16.1.1
[AR1-ospf-1]area 0
[AR1-ospf-1-area-0.0.0.0]ne
[AR1-ospf-1-area-0.0.0.0]network 172.16.1.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]net 123.123.123.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]q
[AR1-ospf-1]q
AR2 {#ar2-2}
[AR2]ospf 1 router-id 172.16.2.2
[AR2-ospf-1]area 0
[AR2-ospf-1-area-0.0.0.0]net 172.16.2.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]net 123.123.123.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]q
[AR2-ospf-1]q
AR3 {#ar3-2}
[AR3]ospf 1 router-id 172.16.3.3
[AR3-ospf-1]area 0
[AR3-ospf-1-area-0.0.0.0]net 172.16.3.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]net 123.123.123.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]q
[AR3-ospf-1]q
配置IKE提议 {#配置ike提议}
AR1 {#ar1-3}
[AR1]ike prop 1
[AR1-ike-proposal-1]dh group5
[AR1-ike-proposal-1]authentication-algorithm sha1
#配置IKEv2协商时所使用的伪随机数产生函数的算法(简称PRF算法)
[AR1-ike-proposal-1]prf aes-xcbc-128
[AR1-ike-proposal-1]q
[AR1]
AR2 {#ar2-3}
[AR2]ike prop 1
[AR2-ike-proposal-1]dh group5
[AR2-ike-proposal-1]authentication-algorithm sha1
[AR2-ike-proposal-1]prf aes-xcbc-128
[AR2-ike-proposal-1]q
AR3 {#ar3-3}
[AR3]ike prop 1
[AR3-ike-proposal-1]dh group5
[AR3-ike-proposal-1]authentication-algorithm sha1
[AR3-ike-proposal-1]prf aes-xcbc-128
[AR3-ike-proposal-1]q
配置IKE对等体 {#配置ike对等体}
AR1 {#ar1-4}
[AR1]ike peer 1 v2
[AR1-ike-peer-1]ike-proposal 1
[AR1-ike-peer-1]pre-shared-key cipher 20wl
#配置IKE对等体中的DPD检测模式
[AR1-ike-peer-1]dpd type periodic
#配置IKE对等体的DPD空闲时间40秒
[AR1-ike-peer-1]dpd idle-time 40
[AR1-ike-peer-1]q
AR2 {#ar2-4}
[AR2]ike peer 1 v2
[AR2-ike-peer-1]ike-proposal 1
[AR2-ike-peer-1]pre-shared-key cipher 20wl
[AR2-ike-peer-1]dpd type periodic
[AR2-ike-peer-1]dpd idle-time 40
[AR2-ike-peer-1]q
AR3 {#ar3-4}
[AR3]ike peer 1 v2
[AR3-ike-peer-1]ike-proposal 1
[AR3-ike-peer-1]pre-shared-key cipher 20wl
[AR3-ike-peer-1]dpd type periodic
[AR3-ike-peer-1]dpd idle-time 40
[AR3-ike-peer-1]q
创建安全提议 {#创建安全提议}
AR1 {#ar1-5}
[AR1]ipsec prop 1
#配置IPSec安全提议使用的安全协议
[AR1-ipsec-proposal-1]transform ah-esp
#配置AH协议使用的认证算法
[AR1-ipsec-proposal-1]ah authentication-algorithm sha2-256
[AR1-ipsec-proposal-1]esp authentication-algorithm sha2-256
[AR1-ipsec-proposal-1]esp encryption-algorithm aes-192
[AR1-ipsec-proposal-1]q
AR2 {#ar2-5}
[AR2]ipsec prop 1
[AR2-ipsec-proposal-1]transform ah-esp
[AR2-ipsec-proposal-1]ah authentication-algorithm sha2-256
[AR2-ipsec-proposal-1]esp authentication-algorithm sha2-256
[AR2-ipsec-proposal-1]esp encryption-algorithm aes-192
[AR2-ipsec-proposal-1]q
AR3 {#ar3-5}
[AR3]ipsec prop 1
[AR3-ipsec-proposal-1]transform ah-esp
[AR3-ipsec-proposal-1]ah authentication-algorithm sha2-256
[AR3-ipsec-proposal-1]esp authentication-algorithm sha2-256
[AR3-ipsec-proposal-1]esp encryption-algorithm aes-192
[AR3-ipsec-proposal-1]q
配置安全框架 {#配置安全框架}
AR1 {#ar1-6}
[AR1]ipsec profile 1
[AR1-ipsec-profile-1]ike-peer 1
[AR1-ipsec-profile-1]proposal 1
[AR1-ipsec-profile-1]q
AR2 {#ar2-6}
[AR2]ipsec profile 1
[AR2-ipsec-profile-1]ike-peer 1
[AR2-ipsec-profile-1]proposal 1
[AR2-ipsec-profile-1]q
AR3 {#ar3-6}
[AR3]ipsec profile 1
[AR3-ipsec-profile-1]ike-peer 1
[AR3-ipsec-profile-1]proposal 1
[AR3-ipsec-profile-1]q
配置Tunnel接口 {#配置tunnel接口}
AR1 {#ar1-7}
[AR1]int t0/0/0
[AR1-Tunnel0/0/0]tunnel-protocol gre p2mp
[AR1-Tunnel0/0/0]source g0/0/0
#开启将动态注册的分支加入NHRP组播成员表功能
[AR1-Tunnel0/0/0]nhrp entry multicast dynamic
#设置OSPF接口的网络类型
[AR1-Tunnel0/0/0]ospf network-type p2mp
#NHRP redirect功能
[AR1-Tunnel0/0/0]nhrp redirect
#在Tunnel接口上应用IPSec安全框架
[AR1-Tunnel0/0/0]ipsec profile 1
[AR1-Tunnel0/0/0]q
AR2 {#ar2-7}
[AR2]int t0/0/0
[AR2-Tunnel0/0/0]tunnel-protocol gre p2mp
[AR2-Tunnel0/0/0]source g0/0/1
#指定tunnel接口地址和官网地址,总部节点上生成关于本分支节点的NHRP peer表项。
[AR2-Tunnel0/0/0]nhrp entry 123.123.123.1 10.1.1.1 register
[AR2-Tunnel0/0/0]ospf network-type p2mp
#NHRP shortcut功能
[AR2-Tunnel0/0/0]nhrp shortcut
[AR2-Tunnel0/0/0]ipsec profile 1
[AR2-Tunnel0/0/0]q
AR3 {#ar3-7}
[AR3]int t0/0/0
[AR3-Tunnel0/0/0]tunnel-protocol gre p2mp
[AR3-Tunnel0/0/0]source g0/0/1
[AR3-Tunnel0/0/0]nhrp entry 123.123.123.1 10.1.1.1 register
[AR3-Tunnel0/0/0]ospf network-type p2mp
[AR3-Tunnel0/0/0]nhrp shortcut
[AR3-Tunnel0/0/0]ipsec profile 1
[AR3-Tunnel0/0/0]q
验证 {#验证}
检查DSVPN配置 {#检查dsvpn配置}
AR1 {#ar1-8}
[AR1]display nhrp peer all
-------------------------------------------------------------------------------
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
-------------------------------------------------------------------------------
123.123.123.2 32 10.1.2.2 123.123.123.2 dynamic route tunnel
-------------------------------------------------------------------------------
Tunnel interface: Tunnel0/0/0
Created time : 00:11:19
Expire time : 01:49:13
-------------------------------------------------------------------------------
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
-------------------------------------------------------------------------------
123.123.123.3 32 10.1.3.3 123.123.123.3 dynamic route tunnel
-------------------------------------------------------------------------------
Tunnel interface: Tunnel0/0/0
Created time : 00:07:31
Expire time : 01:52:56
`Number of nhrp peers: 2
`
AR2 {#ar2-8}
[AR2]display nhrp peer all
-------------------------------------------------------------------------------
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
-------------------------------------------------------------------------------
123.123.123.1 32 10.1.1.1 123.123.123.1 static hub
-------------------------------------------------------------------------------
Tunnel interface: Tunnel0/0/0
Created time : 00:11:27
Expire time : --
`Number of nhrp peers: 1
`
AR3 {#ar3-8}
[AR2]display nhrp peer all
-------------------------------------------------------------------------------
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
-------------------------------------------------------------------------------
123.123.123.1 32 10.1.1.1 123.123.123.1 static hub
-------------------------------------------------------------------------------
Tunnel interface: Tunnel0/0/0
Created time : 00:11:27
Expire time : --
`Number of nhrp peers: 1
`
检查IPSec SA信息 {#检查ipsec-sa信息}
AR1 {#ar1-9}
[AR1]display ipsec sa
===============================
Interface: Tunnel0/0/0
Path MTU: 1500
IPSec profile name: "1"
Mode : PROF-Template
Connection ID : 4
Encapsulation mode: Tunnel
Tunnel local : 10.1.1.1
Tunnel remote : 10.1.3.3
Qos pre-classify : Disable
[Outbound ESP SAs]
SPI: 3091581073 (0xb845c891)
Proposal: ESP-ENCRYPT-AES-192 SHA2-256-128
SA remaining key duration (bytes/sec): 1887433396/2860
Max sent sequence-number: 34
UDP encapsulation used for NAT traversal: N
[Outbound AH SAs]
SPI: 1755157590 (0x689d9456)
Proposal: SHA2-256-128
SA remaining key duration (bytes/sec): 1887436800/2860
Max sent sequence-number: 34
UDP encapsulation used for NAT traversal: N
[Inbound AH SAs]
SPI: 1133922043 (0x439646fb)
Proposal: SHA2-256-128
SA remaining key duration (bytes/sec): 1887436800/2860
Max received sequence-number: 30
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
[Inbound ESP SAs]
SPI: 3135250784 (0xbae02160)
Proposal: ESP-ENCRYPT-AES-192 SHA2-256-128
SA remaining key duration (bytes/sec): 1887433944/2860
Max received sequence-number: 30
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
IPSec profile name: "1"
Mode : PROF-Template
Connection ID : 2
Encapsulation mode: Tunnel
Tunnel local : 10.1.1.1
Tunnel remote : 10.1.2.2
Qos pre-classify : Disable
[Outbound ESP SAs]
SPI: 2677832054 (0x9f9c7976)
Proposal: ESP-ENCRYPT-AES-192 SHA2-256-128
SA remaining key duration (bytes/sec): 1887432440/2636
Max sent sequence-number: 44
UDP encapsulation used for NAT traversal: N
[Outbound AH SAs]
SPI: 345017806 (0x14908dce)
Proposal: SHA2-256-128
SA remaining key duration (bytes/sec): 1887436800/2636
Max sent sequence-number: 44
UDP encapsulation used for NAT traversal: N
[Inbound AH SAs]
SPI: 339028987 (0x14352bfb)
Proposal: SHA2-256-128
SA remaining key duration (bytes/sec): 1887436800/2636
Max received sequence-number: 40
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
[Inbound ESP SAs]
SPI: 3435456947 (0xccc4e9b3)
Proposal: ESP-ENCRYPT-AES-192 SHA2-256-128
SA remaining key duration (bytes/sec): 1887433040/2636
Max received sequence-number: 40
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
AR2 {#ar2-9}
[AR2]display ipsec sa
===============================
Interface: Tunnel0/0/0
Path MTU: 1500
IPSec profile name: "1"
Mode : PROF-ISAKMP
Connection ID : 2
Encapsulation mode: Tunnel
Tunnel local : 10.1.2.2
Tunnel remote : 10.1.1.1
Qos pre-classify : Disable
[Outbound ESP SAs]
SPI: 3435456947 (0xccc4e9b3)
Proposal: ESP-ENCRYPT-AES-192 SHA2-256-128
SA remaining key duration (bytes/sec): 1887433224/2704
Max sent sequence-number: 38
UDP encapsulation used for NAT traversal: N
[Outbound AH SAs]
SPI: 339028987 (0x14352bfb)
Proposal: SHA2-256-128
SA remaining key duration (bytes/sec): 1887436800/2704
Max sent sequence-number: 38
UDP encapsulation used for NAT traversal: N
[Inbound AH SAs]
SPI: 345017806 (0x14908dce)
Proposal: SHA2-256-128
SA remaining key duration (bytes/sec): 1887436800/2704
Max received sequence-number: 41
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
[Inbound ESP SAs]
SPI: 2677832054 (0x9f9c7976)
Proposal: ESP-ENCRYPT-AES-192 SHA2-256-128
SA remaining key duration (bytes/sec): 1887432728/2704
Max received sequence-number: 41
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
AR3 {#ar3-9}
[AR3]display ipsec sa
===============================
Interface: Tunnel0/0/0
Path MTU: 1500
IPSec profile name: "1"
Mode : PROF-ISAKMP
Connection ID : 2
Encapsulation mode: Tunnel
Tunnel local : 10.1.3.3
Tunnel remote : 10.1.1.1
Qos pre-classify : Disable
[Outbound ESP SAs]
SPI: 3135250784 (0xbae02160)
Proposal: ESP-ENCRYPT-AES-192 SHA2-256-128
SA remaining key duration (bytes/sec): 1887433852/2820
Max sent sequence-number: 31
UDP encapsulation used for NAT traversal: N
[Outbound AH SAs]
SPI: 1133922043 (0x439646fb)
Proposal: SHA2-256-128
SA remaining key duration (bytes/sec): 1887436800/2820
Max sent sequence-number: 31
UDP encapsulation used for NAT traversal: N
[Inbound AH SAs]
SPI: 1755157590 (0x689d9456)
Proposal: SHA2-256-128
SA remaining key duration (bytes/sec): 1887436800/2820
Max received sequence-number: 35
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
[Inbound ESP SAs]
SPI: 3091581073 (0xb845c891)
Proposal: ESP-ENCRYPT-AES-192 SHA2-256-128
SA remaining key duration (bytes/sec): 1887433300/2820
Max received sequence-number: 35
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
检查OSPF路由 {#检查ospf路由}
AR1 {#ar1-10}
[AR1]display ospf 1 routing
OSPF Process 1 with Router ID 172.16.1.1
Routing Tables
Routing for Network
Destination Cost Type NextHop AdvRouter Area
123.123.123.1/32 0 Stub 123.123.123.1 172.16.1.1 0.0.0.0
172.16.1.0/24 1 Stub 172.16.1.1 172.16.1.1 0.0.0.0
123.123.123.2/32 1562 Stub 123.123.123.2 172.16.2.2 0.0.0.0
123.123.123.3/32 1562 Stub 123.123.123.3 172.16.3.3 0.0.0.0
172.16.2.0/24 1563 Stub 123.123.123.2 172.16.2.2 0.0.0.0
172.16.3.0/24 1563 Stub 123.123.123.3 172.16.3.3 0.0.0.0
Total Nets: 6
Intra Area: 6 Inter Area: 0 ASE: 0 NSSA: 0
AR2 {#ar2-10}
[AR2]display ospf 1 routing
OSPF Process 1 with Router ID 172.16.2.2
Routing Tables
Routing for Network
Destination Cost Type NextHop AdvRouter Area
123.123.123.2/32 0 Stub 123.123.123.2 172.16.2.2 0.0.0.0
172.16.2.0/24 1 Stub 172.16.2.2 172.16.2.2 0.0.0.0
123.123.123.1/32 1562 Stub 123.123.123.1 172.16.1.1 0.0.0.0
123.123.123.3/32 3124 Stub 123.123.123.1 172.16.3.3 0.0.0.0
172.16.1.0/24 1563 Stub 123.123.123.1 172.16.1.1 0.0.0.0
172.16.3.0/24 3125 Stub 123.123.123.1 172.16.3.3 0.0.0.0
Total Nets: 6
Intra Area: 6 Inter Area: 0 ASE: 0 NSSA: 0
AR3 {#ar3-10}
[AR3]display ospf 1 routing
OSPF Process 1 with Router ID 172.16.3.3
Routing Tables
Routing for Network
Destination Cost Type NextHop AdvRouter Area
123.123.123.3/32 0 Stub 123.123.123.3 172.16.3.3 0.0.0.0
172.16.3.0/24 1 Stub 172.16.3.3 172.16.3.3 0.0.0.0
123.123.123.1/32 1562 Stub 123.123.123.1 172.16.1.1 0.0.0.0
123.123.123.2/32 3124 Stub 123.123.123.1 172.16.2.2 0.0.0.0
172.16.1.0/24 1563 Stub 123.123.123.1 172.16.1.1 0.0.0.0
172.16.2.0/24 3125 Stub 123.123.123.1 172.16.2.2 0.0.0.0
Total Nets: 6
Intra Area: 6 Inter Area: 0 ASE: 0 NSSA: 0
执行ping操作,查看配置结果 {#执行ping操作,查看配置结果}
AR2 {#ar2-11}
[AR2]ping -a 172.16.2.2 172.16.3.3
PING 172.16.3.3: 56 data bytes, press CTRL_C to break
Reply from 172.16.3.3: bytes=56 Sequence=1 ttl=255 time=30 ms
Reply from 172.16.3.3: bytes=56 Sequence=2 ttl=255 time=20 ms
Reply from 172.16.3.3: bytes=56 Sequence=3 ttl=255 time=30 ms
Reply from 172.16.3.3: bytes=56 Sequence=4 ttl=255 time=30 ms
Reply from 172.16.3.3: bytes=56 Sequence=5 ttl=255 time=30 ms
--- 172.16.3.3 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/28/30 ms
[AR2]display nhrp peer all
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
123.123.123.1 32 10.1.1.1 123.123.123.1 static hub
Tunnel interface: Tunnel0/0/0
Created time : 00:55:09
Expire time : --
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
123.123.123.3 32 10.1.3.3 123.123.123.3 dynamic route tunnel
Tunnel interface: Tunnel0/0/0
Created time : 00:21:48
Expire time : 01:38:30
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
123.123.123.2 32 10.1.2.2 123.123.123.2 dynamic local
Tunnel interface: Tunnel0/0/0
Created time : 00:21:48
Expire time : 01:38:12
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
172.16.2.20 24 10.1.2.2 123.123.123.2 dynamic local
Tunnel interface: Tunnel0/0/0
Created time : 00:21:30
Expire time : 01:38:30
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
172.16.3.3 32 10.1.3.3 123.123.123.3 dynamic route network
Tunnel interface: Tunnel0/0/0
Created time : 00:16:46
Expire time : 01:43:14
Protocol-addr Mask NBMA-addr NextHop-addr Type Flag
172.16.3.10 24 10.1.3.3 123.123.123.3 dynamic route network
Tunnel interface: Tunnel0/0/0
Created time : 00:12:21
Expire time : 01:47:39
Number of nhrp peers: 6 [AR2]
 51工具盒子
51工具盒子